How Azure Application Gateway with WAF Saved My Client’s Digital Platform
As a Cloud Architect, I’ve worked with organizations of all sizes—but one experience I often share was with a humble, family-run bakery in Sri Lanka that made a bold move: taking their entire business online.
Their brand, let me name it as "Golden Loaf" 
Within weeks of going live, their internal IT team started flagging issues:
It didn’t take long to confirm: they were under active attack.
The application was open to SQL injection, cross-site scripting (XSS), and bot traffic probing for vulnerabilities. While their developers had done a great job, they hadn’t yet implemented enterprise-grade edge protection.
My Solution: Azure Application Gateway + WAF v2 + Azure DDoS
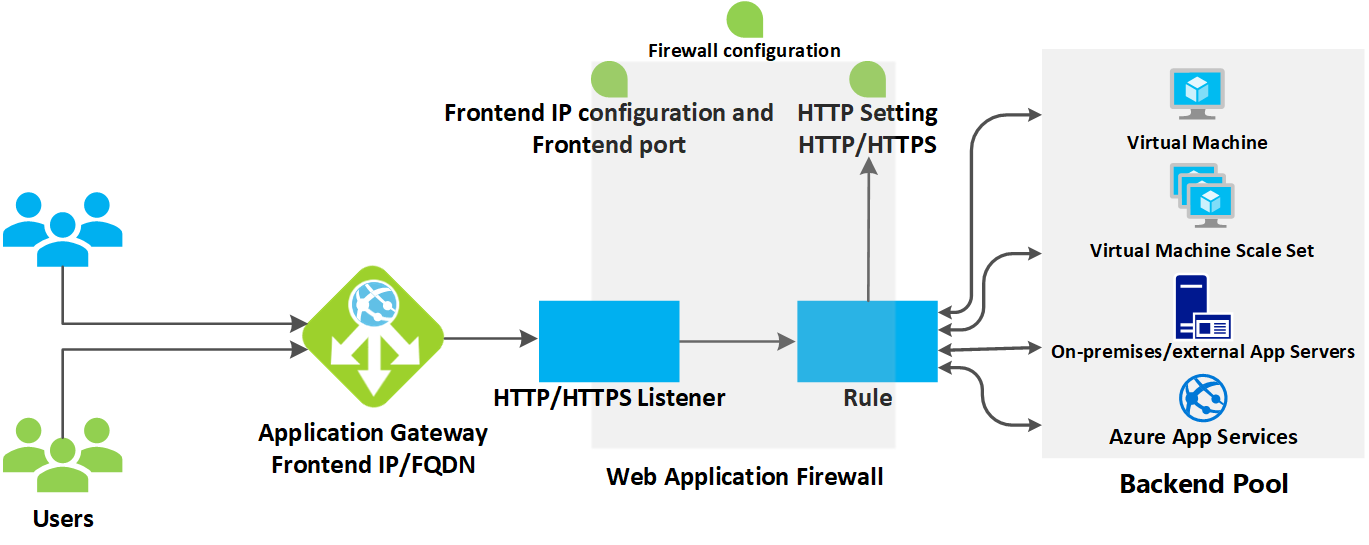
To secure the platform without redesigning it, I proposed a solution built on Azure Application Gateway with Web Application Firewall (WAF v2).
What changed?
The owners of Golden Loaf were amazed—not only was their website fast and reliable, it was secure and resilient.
So what is Microsoft Azure Application Gateway + Web APplication Firewall?
Microsoft Azure Application Gateway is a powerful, application-level web traffic load balancer that not only distributes incoming traffic across your services, but also enhances your security posture and performance through advanced, layered features. Here’s an in-depth look at how it safeguards and optimizes modern web applications.
Main Features of Application Gateway for protection of the application are following:
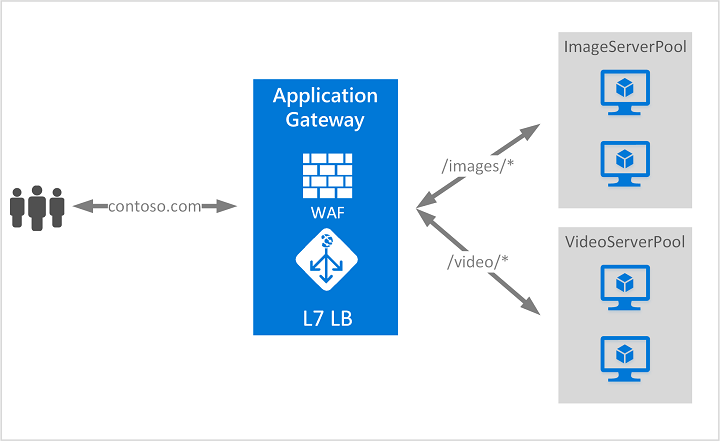
Protecting your Web Applications
These are the following ways to protect and secure your Web Applications:
1. Web Application Firewall (WAF)
- Integrated Security: Azure Application Gateway features a built-in Web Application Firewall (WAF), designed to protect web applications from common threats such as SQL injection, cross-site scripting (XSS), and other vulnerabilities outlined in the OWASP Top 10. Attacks That Azure WAF on Application Gateway Can Overcome
So the above depends either we are choosing a detection feaure or the preventive feature
- Custom Policy & Rules: WAF policies can be tailored for each site, listener, or routing rule, providing site-specific protection and the ability to customize or exclude particular rules to minimize false positives.
- Real-Time Monitoring: Logs attacks and alerts through Azure Monitor, providing transparency, auditability, and integration with Microsoft Defender for Cloud for a unified security dashboard
- Bot and DDoS Defense: Includes intelligent defenses against malicious bots and distributed denial-of-service (DDoS) attacks, with IP reputation rule sets and Azure DDoS Protection integration. this is an additional resource (Azure DDoS Protection) that needs to be deployed to ensure more security
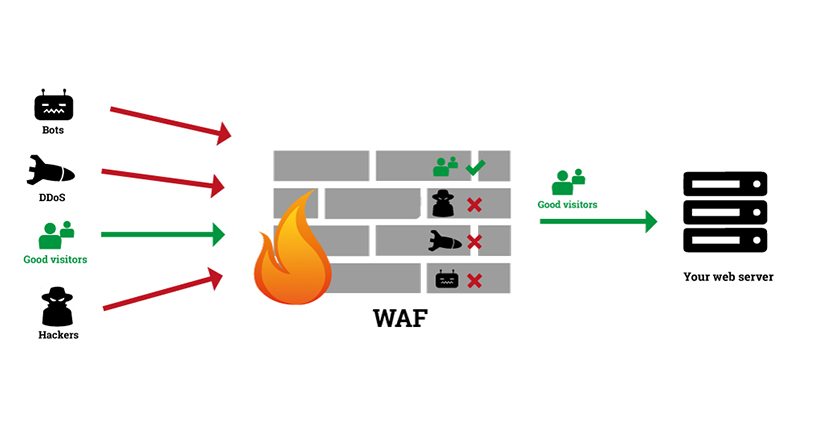
- Rate Limiting & Throttling: Controls to prevent abuse from traffic spikes or malicious automated sources, further securing backend resources
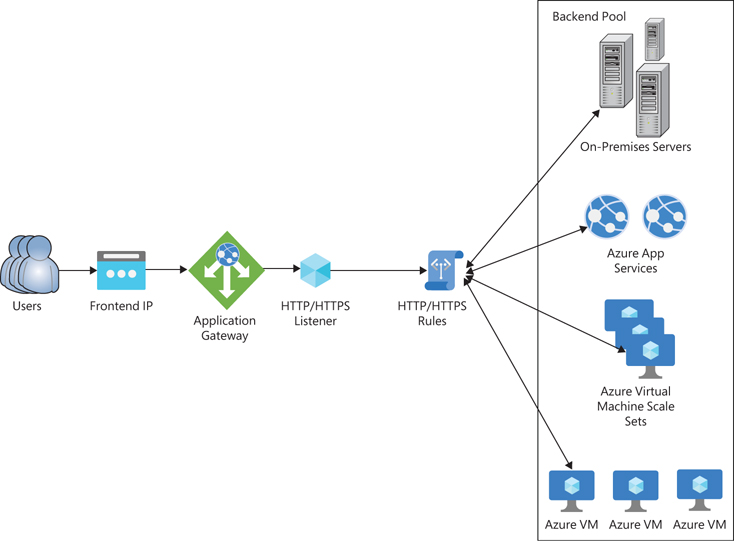
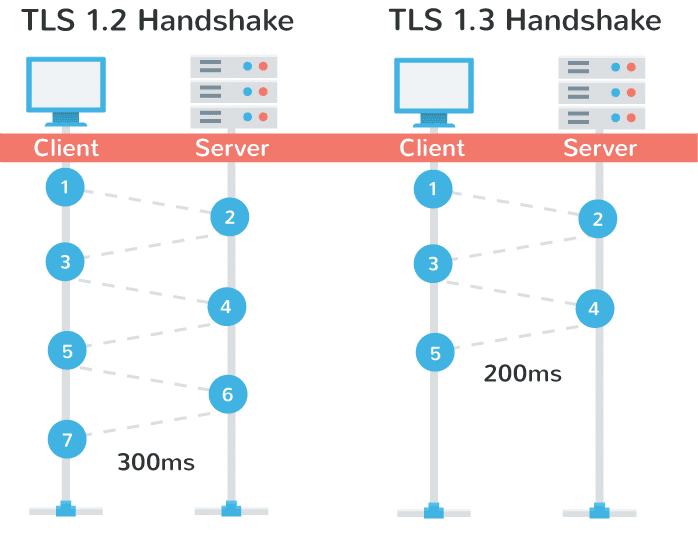
2. End-to-End SSL/TLS Encryption
- SSL Termination & Offload: Decrypts incoming SSL/TLS traffic at the gateway, offloading resource-intensive encryption from backend servers
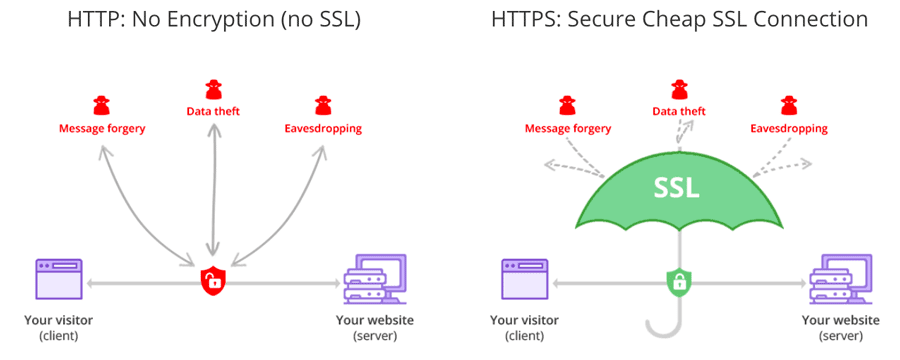
- End-to-End Security: Optional full encryption—re-encrypting traffic between the gateway and your backend—meets compliance and privacy requirements
3. Advanced Layer 7 Security Features
- Session Affinity: Uses cookies to pin a user session to a specific backend, helping mitigate session hijacking risks
- Geo-Filtering & Custom Rules: Blocks or allows access by geographic region and applies custom inspection logic, adding additional gates against unauthorized access
Optimization: Enhancing Performance & Availability
These are the following ways to optimiize the performance and availability of the network or the application:
1. Intelligent Load Balancing
- Layer 7 Awareness: Makes routing decisions based on HTTP request attributes—like URI path, headers, and host—ideal for microservices and modular apps
- Custom Routing Rules:
- -> Multi-site Hosting: Host and manage multiple domains or sites under a single Application Gateway instance, with discrete routing and policies for each
- -> URL Path-Based Routing: Direct specific URLs to different backend services or microservices
- Health Probes: Constantly monitors backend server health and reroutes traffic away from unhealthy instances, maintaining uptime and reliability
2. Scalability and High Availability
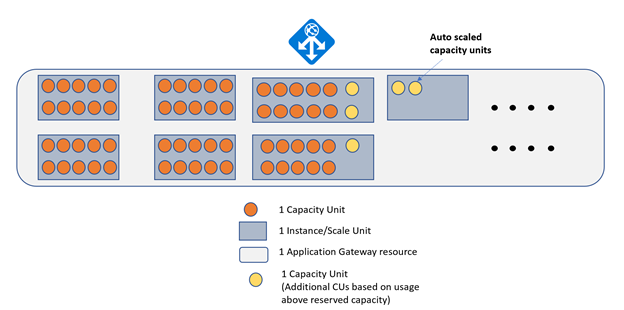
- Autoscaling: Dynamically scales up or down based on real-time traffic needs—no manual reconfiguration required. Handles sudden spikes and reduces costs during low-traffic periods
- Zone Redundancy: Supports deployment across multiple availability zones for robust fault tolerance and disaster recovery
3. Performance Optimization
- SSL/TLS Offloading: Frees backend compute resources, allowing applications to serve more requests with lower latency
- Header and URL Rewriting: Modifies HTTP/HTTPS requests and responses on the fly, enabling complex routing, redirects, and improved traffic management
- HTTP/2 & WebSocket Support: Facilitates faster page loads and more efficient communication for modern, real-time web apps
4. Deep Monitoring & Diagnostics
- Integration with Azure Monitor & Log Analytics: Gain visibility into throughput, health metrics, attack trends, and backend performance, empowering data-driven tuning
- Proactive Problem Detection: Real-time alerts support rapid troubleshooting and threat mitigation

These are scenarios what I have worked on:
These are the following ways to optimiize the performance and availability of the network or the application:
Project Experience 1:
I have secured numerous backend APIs by integrating Azure Web Application Firewall (WAF) policies with Application Gateway. This setup enabled deep packet inspection, protection against OWASP Top 10 vulnerabilities, and access control based on request headers, IP restrictions, and geolocation. I’ve also implemented routing strategies based on API versioning and business context to manage changes and ensure backward compatibility.
Project Experience 2:
In projects involving microservices-based application deployments, I utilized Application Gateway's path-based and host-based routing capabilities to direct users to the appropriate microservice. This ensured clean separation of services, ease of maintenance, and better performance. I also leveraged custom headers for intelligent routing, which played a key role in handling user authentication and session persistence across services.
Project Experience 3:
I have been involved in seamlessly transitioning legacy on-premise systems to modern cloud-based infrastructures using Azure Application Gateway. This included designing secure routing mechanisms, implementing SSL termination, and ensuring high availability without compromising on performance. These migrations not only preserved critical business logic but also enabled enhanced scalability and integration with modern services.
Project Experience 4:
For globally distributed applications, I configured Azure Application Gateway with custom probes and multi-region backend pools. This allowed traffic to be routed intelligently to the nearest healthy endpoint based on user location, significantly reducing latency and ensuring business continuity. I’ve worked on solutions that maintained performance SLAs and supported geo-redundancy and failover strategies across continents.
Conclusion
I believe that rather than expecting to receive secure traffic its always better to prepare your environment in a safe and secured manner
Azure Application Gateway is much more than a traditional load balancer. It is a comprehensive tool for protecting and optimizing your web applications—combining cutting-edge security like WAF, DDoS defense, and SSL offloading with intelligent traffic management, advanced routing, autoscaling, and deep diagnostics. By adopting Application Gateway, organizations can achieve scalable, resilient, and secure cloud architectures fit for today’s demanding web workloads