The world is moving towards SaaS offerings rather than IaaS — authentication must modernize too
In the early days of cloud adoption, Infrastructure as a Service (IaaS) dominated the scene. Organizations moved their on-premises servers into cloud-hosted virtual machines. The authentication model remained largely the same:
- Traditional Active Directory
- VPN-based access
- Network perimeter-based trust (“If you’re inside, you’re trusted”)
But that’s changing — and fast.
In a SaaS-first world, identity becomes the new perimeter. There is no longer a single “inside” network to protect. Employees, partners, and contractors may access business applications from any device, anywhere in the world. This makes the authentication process the single, most critical gatekeeper for sensitive data. Modern identity platforms like Microsoft Entra ID support authentication protocols such as OAuth 2.0, OpenID Connect, and SAML, which are designed for secure, internet-facing applications that operate outside the traditional network boundary.
This shift also makes Zero Trust security a necessity rather than an optional enhancement. In a Zero Trust model, no user or device is automatically trusted — even if they are on the company’s network. Access is granted dynamically based on multiple factors, such as the user’s role, device compliance, location, and the sensitivity of the data being accessed. Conditional Access policies in Microsoft Entra ID make this possible, allowing organizations to create adaptive, risk-based authentication flows that balance security and usability.
As workloads move away from IaaS-hosted monolithic systems towards SaaS-first architectures, authentication must evolve from being network-based to identity-based.
That’s why cloud identity services like Microsoft Entra ID are not just “add-ons” anymore — they’re the backbone of secure, modern business operations.
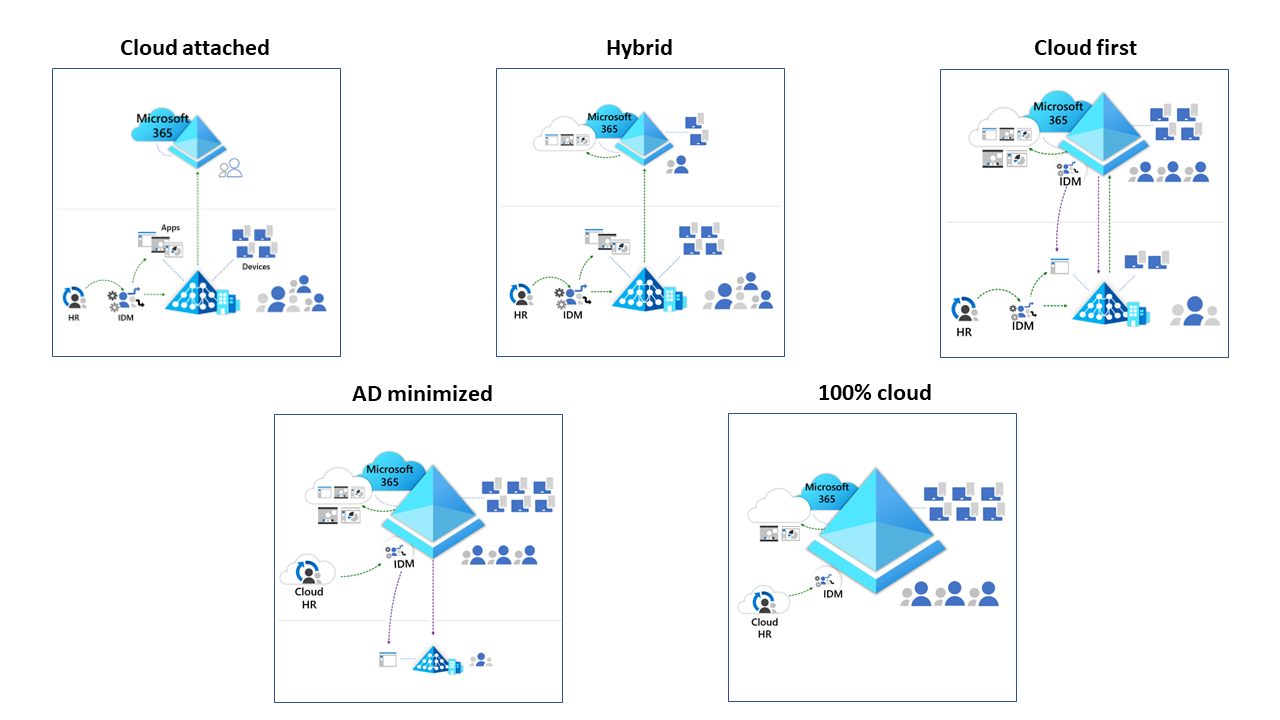
With SaaS adoption comes a dramatic expansion of the attack surface. Credential theft, phishing, and account takeover attacks have surged in recent years, targeting weak or reused passwords. As a result, modern authentication must go beyond passwords. Multifactor authentication (MFA), biometrics, and passwordless sign-ins significantly reduce the risk of unauthorized access. Microsoft Entra ID integrates these capabilities, ensuring that even if a password is compromised, attackers cannot gain access without additional verification.
Finally, centralized identity management is key for governance and compliance in a SaaS-driven environment. When every application has its own separate login and permission model, controlling access becomes chaotic. By integrating SaaS applications into a single identity platform, organizations can manage user roles, automate provisioning and deprovisioning, and generate detailed audit logs for compliance reporting. This not only strengthens security but also streamlines operations, making identity the foundation of modern enterprise security strategies.
From Chaos to Control: My Real-World Journey with Microsoft Entra ID
When people ask me what the most critical pillar of cloud security is, I don’t even blink before answering: Identity.
During one of my biggest Azure migration projects last year, I walked into an organization where identity management was… let’s just say “loosely managed.” People had multiple logins, permissions were handed out like candy, and security relied on the hope that “nothing bad will happen.”
Hope, unfortunately, is not a security strategy.
That’s when Microsoft Entra ID became our transformation engine.
The Problem they faced
The client’s goal wasn’t just to clean this up — they wanted a scalable identity solution that could secure hybrid workloads, enforce Zero Trust, and make user access simple but safe after the the recommendation discussion with me.
What is Microsoft Entra ID?
Before I explain the journey, here’s a quick definition for anyone new:
Microsoft Entra ID (formerly Azure Active Directory) is Microsoft’s cloud-based identity and access management service. It controls who can access your applications, data, and resources, and enforces security policies based on identity, device, and context.
Identity is the first pillar of Zero Trust.
Think of it as your digital security guard, checking IDs at every entrance and making sure only the right people get in — with the right level of access.
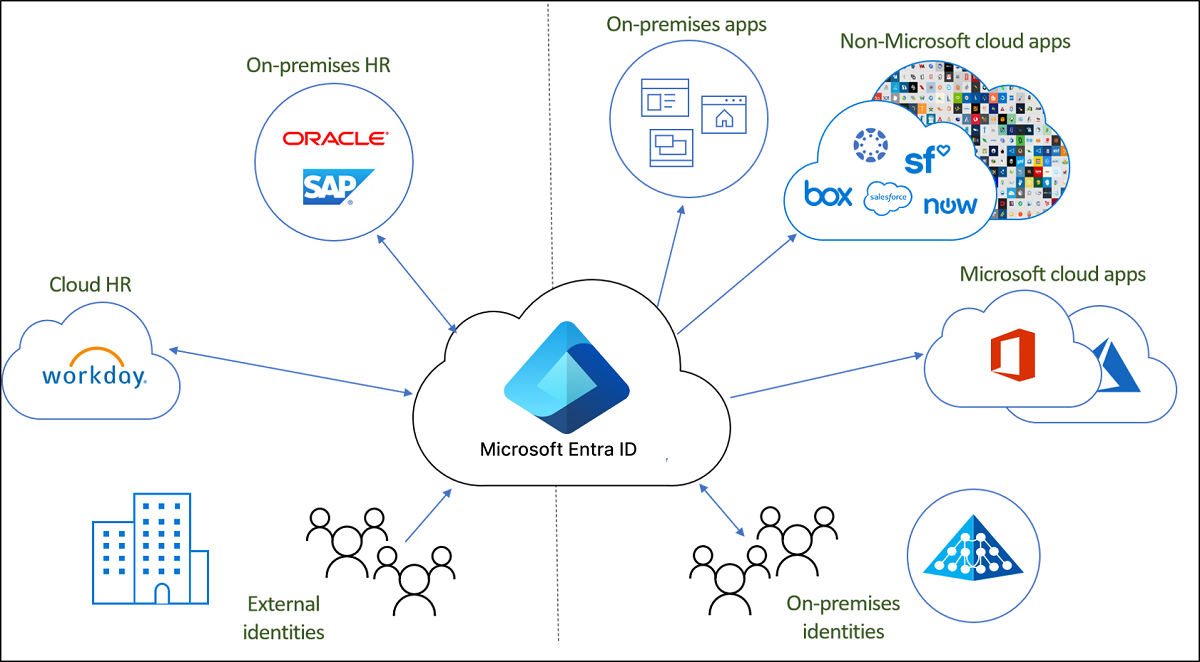
Key Terms You’ll Hear with Entra ID
Our Implementation Journey - Outcomes
This is an AI Generated Image: by M. Ashfarq Kariapper
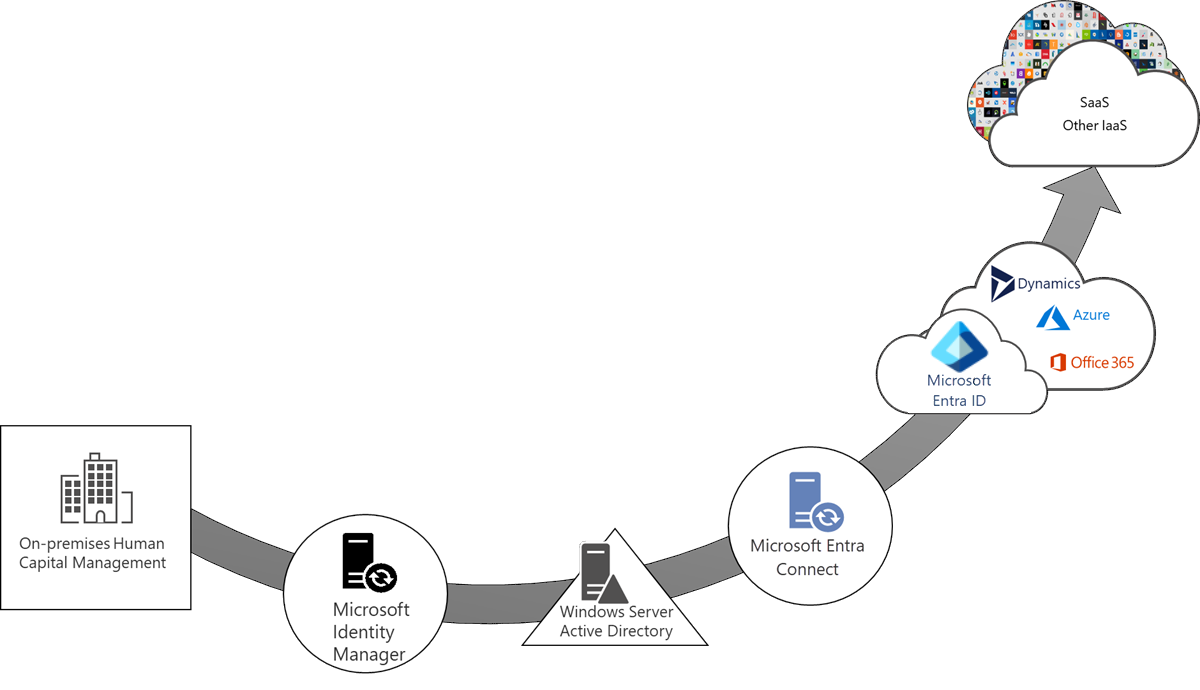
We deployed Azure AD Connect to sync on-prem AD accounts into Entra ID.
- Filtered only active OUs to avoid junk accounts in the cloud.
- Implemented Password Hash Sync to unify credentials.
Before as a precautionary measure, we understood that over-syncing is dangerous. As old, unused accounts are a hacker’s dream entry point.
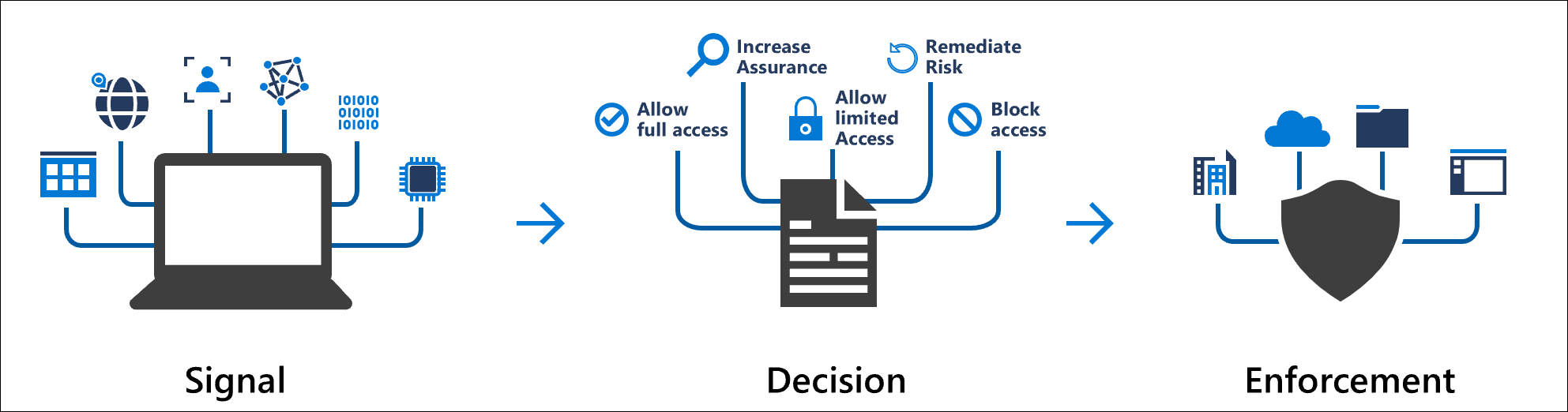
We crafted policies to enforce:
- MFA for all external logins and privileged accounts.
- Location-based restrictions (block logins from countries where the business doesn’t operate).
- Device compliance checks (only corporate devices can access sensitive apps).
This impacted the process of 72% reduction in suspicious sign-ins within the first month.
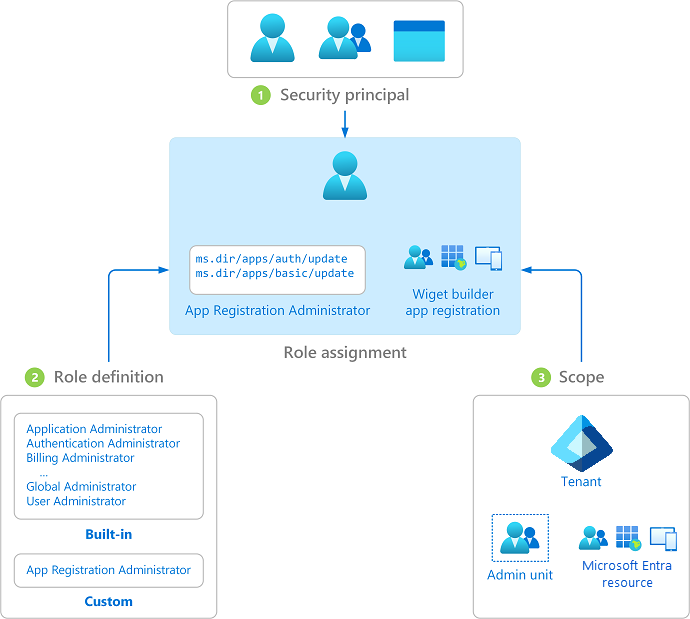
We broke the habit of giving everyone “Admin” rights:
- Created custom roles for finance, HR, and marketing.
- Used groups to assign permissions in bulk — easier to manage than individual assignments.
The access violations dropped to nearly zero.
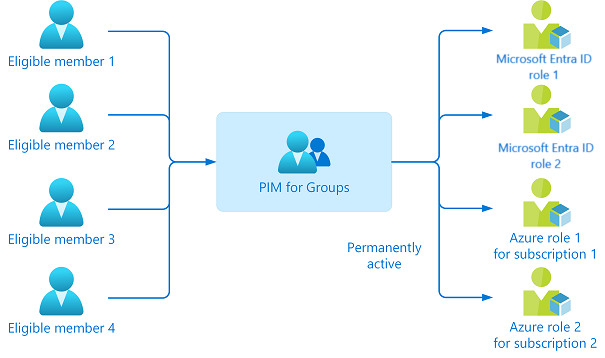
Admins now request just-in-time access to elevated roles for a limited period.
- Every activation requires MFA.
- All actions are logged for auditing.
This process reduced the normal saying of “God, forgot to remove admin rights 😉 ” incidents.
We integrated 50+ apps (Microsoft 365, SAP, Salesforce, HR tools, even custom apps) into the Entra ID portal.
- Users log in once and access everything from one dashboard.
This reduced the Password reset tickets by 40%.
We also proposed Entra ID for the following
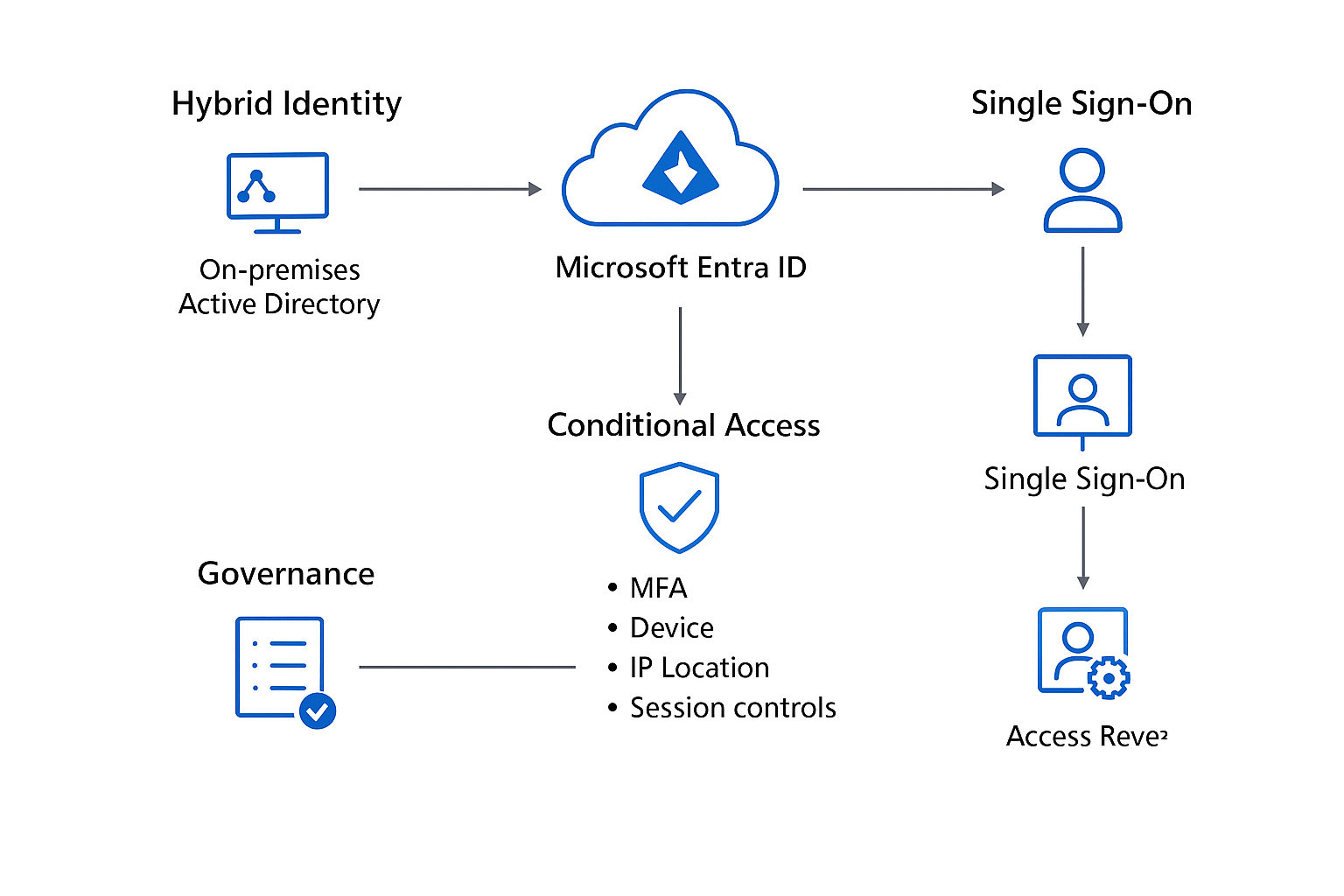
Achieving Security, Governance, and Compliance with Entra ID
Zero Trust Approach – Verify explicitly, use least privilege, and assume breach.
MFA Everywhere – Especially for high-value accounts.
-
Identity Protection – Detect leaked credentials and high-risk sign-ins automatically.
Session Controls – Limit session duration for sensitive apps.
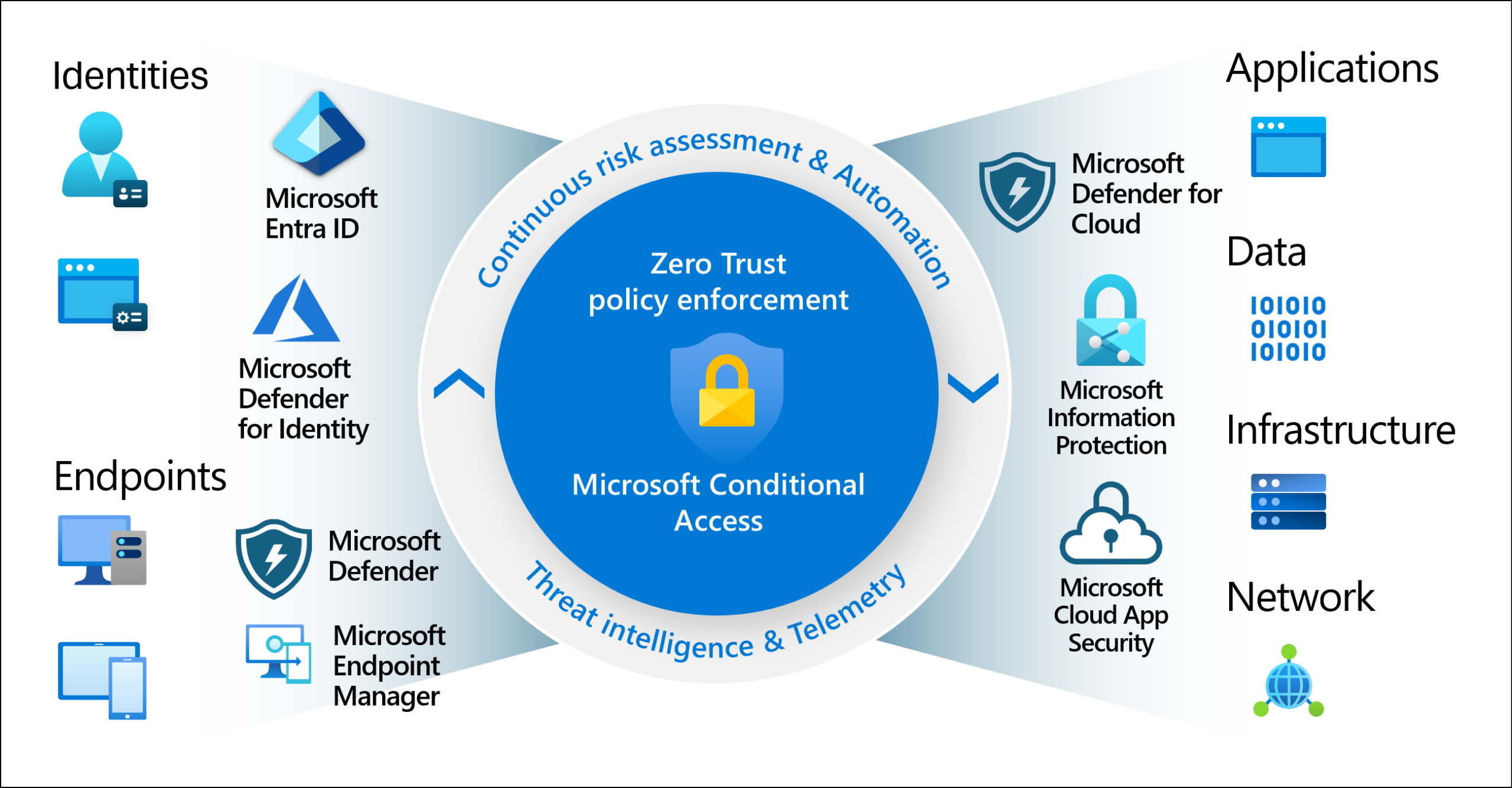
- Access Reviews – Regular audits built into the system.
- PIM – Time-bound, just-in-time admin rights
- RBAC & Groups – Structured access instead of chaotic, individual assignments.
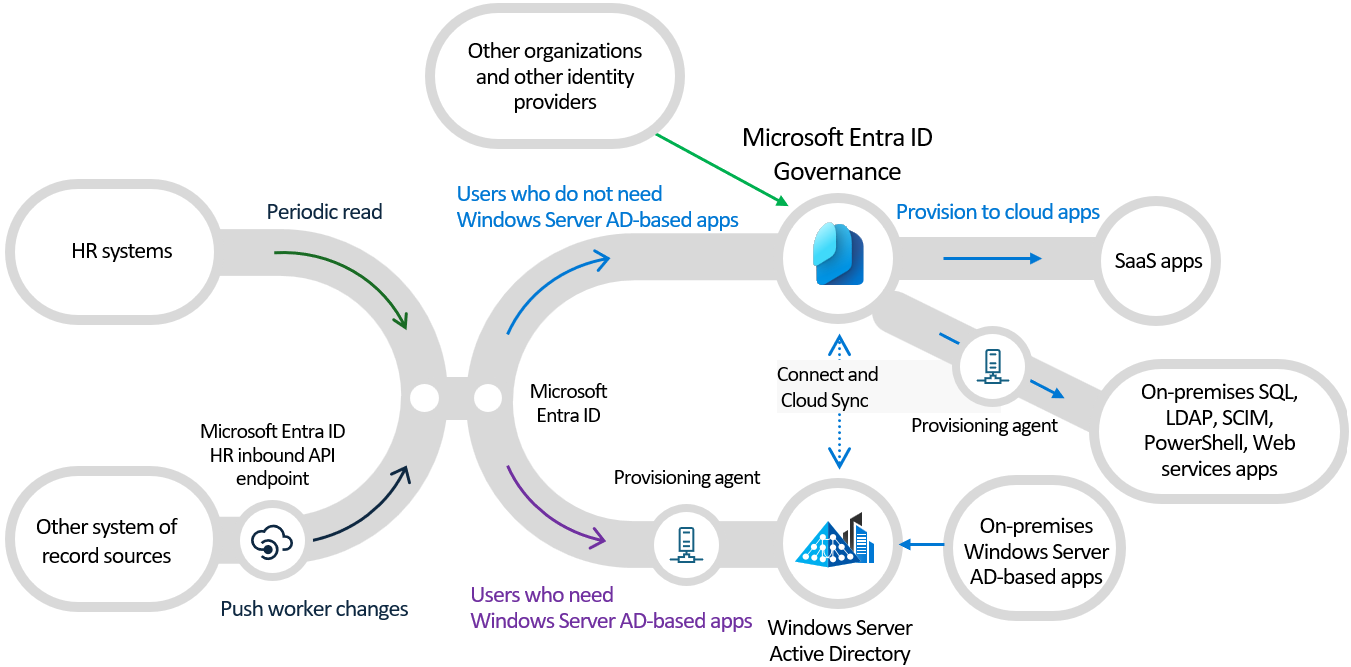
- Conditional Access – Meet compliance requirements by enforcing device health, location checks, and MFA.
Audit Logs & Reports – Detailed tracking for compliance audits.
Data Residency – Keep user identity data stored within your region if regulations require.
Integration with Microsoft Purview – Extend compliance controls to identity-related data.
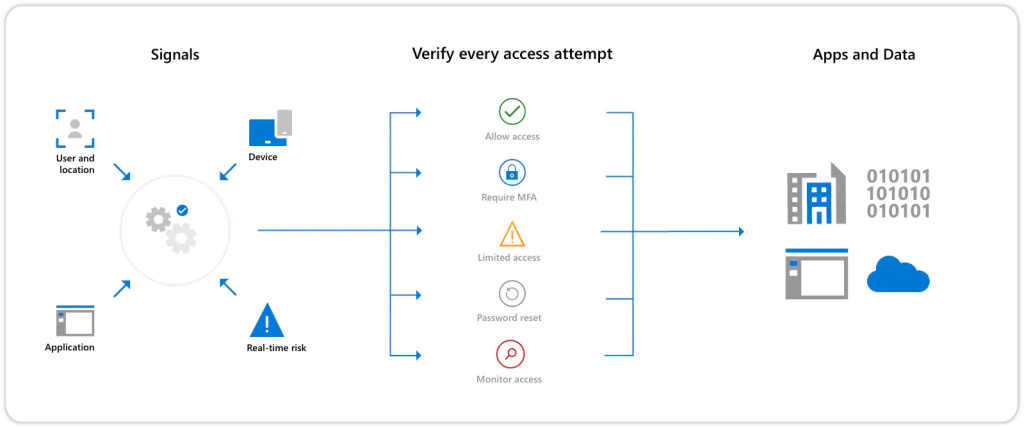
The Outcome
- Zero unauthorized access incidents.
- 40% fewer support tickets.
Full audit readiness with clear logs of who accessed what and when.
And perhaps my favorite win: The CEO, who used to have three different passwords for three different business apps, now logs in once in the morning — and never has to think about it again.
Even O365 uses the Microsft Entra ID to manage and govern the Identities
If you’re serious about security, governance, and compliance, start with identity. Everything else in your cloud security strategy builds on that foundation.
Microsoft Entra ID isn’t just about logging in — it’s about owning your identity layer, enforcing secure access, and keeping governance in the hands of IT, not in the shadows of employees’ notebooks.


