Securing the Cloud: My Hands-On Journey with Azure Firewall
In the ever-evolving landscape of cloud security, safeguarding digital assets is both a necessity and a challenge. Recently, I had the unique opportunity to work closely with a customer who was migrating critical workloads to Microsoft Azure. Their primary concern—and mine—was securing their cloud environment effectively. This hands-on journey with Azure Firewall was eye-opening and filled with valuable lessons that I want to share.
Understanding Azure Firewall vs. Traditional Firewalls
At the outset, one of the major conversations with the customer was about how Azure Firewall differs from traditional firewalls. Unlike conventional hardware-based firewalls, Azure Firewall is a cloud-native, fully stateful firewall-as-a-service. This means it is designed to seamlessly integrate into the Azure ecosystem, providing scalability without the need for physical appliances or complex configurations.
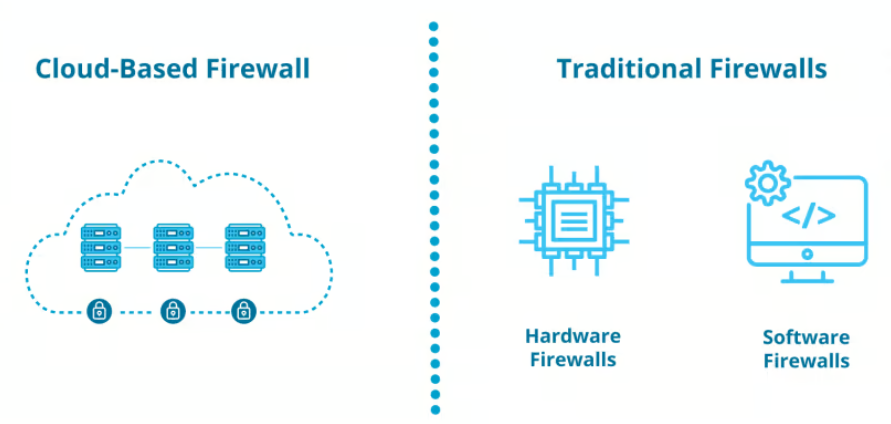
Traditional firewalls often require manual scaling and can become bottlenecks under high traffic. Azure Firewall, on the other hand, automatically scales based on your network traffic and demands, eliminating the risk of resource exhaustion. It also supports both inbound and outbound filtering rules, along with threat intelligence-based filtering to detect and block known malicious IP addresses and domains in real time.
Key Value Adds from Azure Firewall
The customer's cloud environment spanned multiple virtual networks across regions, and this complexity underscored the value Azure Firewall added:
- Centralized Management: Azure Firewall’s seamless integration with Azure Monitor and Azure Security Center meant we could monitor and manage all firewall rules and logs centrally. This visibility was crucial for compliance and troubleshooting.
- Application and Network Rule Filtering: Unlike some basic cloud firewalls, Azure Firewall allowed us to create granular policies for traffic filtering, both at the network level (IP addresses, ports) and the application level (URLs, HTTP/S traffic).
- Fully Stateful and High Availability: With built-in high availability and cloud scalability features, there was no single point of failure, providing the customer peace of mind and operational continuity.
- Threat Intelligence Integration: The ability to leverage Microsoft’s threat intelligence feed meant proactive blocking of emerging threats without manual intervention.
What is Azure Firewall?
Azure Firewall is a cloud-native, intelligent network firewall security service that offers top-tier threat protection for your Azure cloud workloads. It is a fully stateful firewall as a service, featuring built-in high availability and unlimited cloud scalability. Azure Firewall inspects both east-west and north-south traffic.
Azure Firewall is available in three SKUs: Basic, Standard, and Premium.
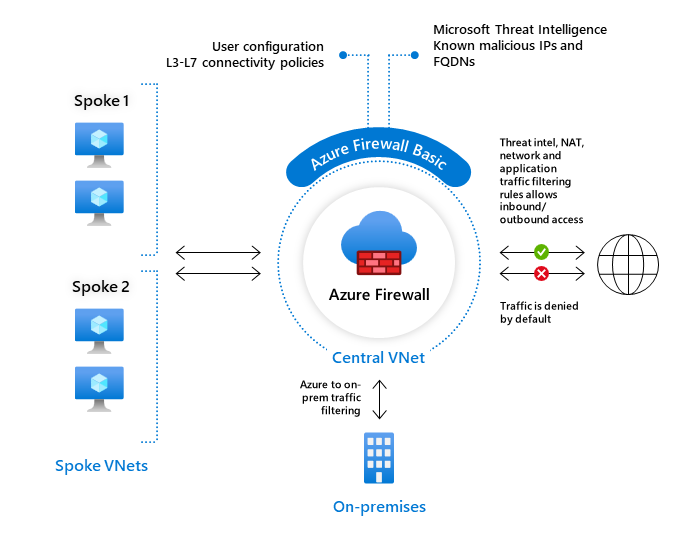
Azure Firewall Basic
Azure Firewall Basic is designed for small and medium-sized businesses (SMBs) to secure their Azure cloud environments. It provides essential protection at an affordable price..
Azure Firewall Basic includes the following features:
- Built-in High Availability - no extra load balancers are required and there's nothing you need to configure.
- Availability Zones
- Application FQDN filtering rules - can limit outbound HTTP/S traffic or Azure SQL traffic to a specified list of fully qualified domain names (FQDN) including wild cards. This feature doesn't require Transport Layer Security (TLS) termination
- Network traffic filtering rules - centrally create allow or deny network filtering rules by source and destination IP address, port, and protocol.
- FQDN tags - An FQDN tag represents a group of fully qualified domain names (FQDNs) associated with well known Microsoft services. You can use an FQDN tag in application rules to allow the required outbound network traffic through your firewall.
- Service tags
- Threat intelligence in alert mode - Threat intelligence-based filtering can be enabled for your firewall to alert traffic from/to known malicious IP addresses and domains. The IP addresses and domains are sourced from the Microsoft Threat Intelligence feed.
- Outbound SNAT support - All outbound virtual network traffic IP addresses are translated to the Azure Firewall public IP (Source Network Address Translation). You can identify and allow traffic originating from your virtual network to remote Internet destinations. Azure Firewall doesn't SNAT when the destination IP is a private IP range per IANA RFC 1918
- Inbound DNAT support - Inbound Internet network traffic to your firewall public IP address is translated (Destination Network Address Translation) and filtered to the private IP addresses on your virtual networks.
- Multiple public IP addresses
- Azure Monitor logging
- Certifications
Key limitations of Azure Firewall Basic include:
- Supports Threat Intel alert mode only
- Fixed scale unit with two virtual machine backend instances
- Recommended for environments with an estimated throughput of 250 Mbps
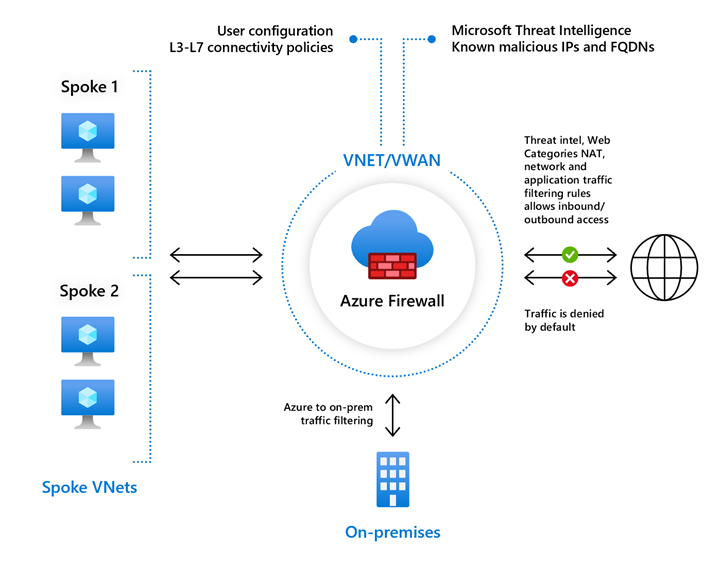
Azure Firewall Standard
Azure Firewall Standard provides L3–L7 filtering along with threat intelligence feeds sourced directly from Microsoft Cyber Security. It can detect and block traffic to or from known malicious IP addresses and domains, with real-time updates to safeguard against new and emerging threats.
Adding to the Azure Firewall Basic Features, it also specially includes:
- Built-in High Availability
- Availability Zones - Azure Firewall can be configured during deployment to span multiple Availability Zones for increased availability. With Availability Zones, your availability increases to 99.99% uptime.
- Unrestricted cloud scalability - Azure Firewall can scale out as much as you need to accommodate changing network traffic flows, so you don't need to budget for your peak traffic.
- Application FQDN filtering rules
- Network traffic filtering rules
- FQDN tags
- Service tags
- Threat intelligence
- DNS proxy
- Custom DNS - Custom DNS allows you to configure Azure Firewall to use your own DNS server, while ensuring the firewall outbound dependencies are still resolved with Azure DNS. You can configure a single DNS server or multiple servers in Azure Firewall and Firewall Policy DNS settings.
- FQDN in network rules - You can use fully qualified domain names (FQDNs) in network rules based on DNS resolution in Azure Firewall and Firewall Policy.
- Deployment without public IP address in Forced Tunnel Mode - Azure Firewall normally requires a public IP for operation, but to avoid direct Internet exposure, it can be deployed in Forced Tunnel mode. This mode uses a management NIC for operations, allows the datapath network to function without a public IP, and can route or block Internet traffic through another firewall. Forced Tunnel mode must be set during deployment or via stop/start reconfiguration, and is always enabled in Secure Hub deployments.
- Outbound SNAT support
- Inbound DNAT support
- Multiple public IP addresses
- Azure Monitor logging - All events are integrated with Azure Monitor, allowing you to archive logs to a storage account, stream events to your event hub, or send them to Azure Monitor logs.
- Forced tunneling - Azure Firewall can be configured to send all Internet-bound traffic to a specified next hop—such as an on-premises edge firewall or network virtual appliance (NVA); for inspection before reaching the Internet.
- Web categories - Web categories let administrators allow or deny user access to web site categories such as gambling websites, social media websites, and others. Web categories are included in Azure Firewall Standard, but it's more fine-tuned in Azure Firewall Premium.
- Certifications - Azure Firewall is Payment Card Industry (PCI), Service Organization Controls (SOC), and International Organization for Standardization (ISO) compliant.
Azure Firewall Premium
Azure Firewall Premium offers advanced capabilities, including signature-based IDPS for rapid attack detection by identifying specific patterns, such as byte sequences in network traffic or malicious instruction sequences used by malware. With over 67,000 signatures in more than 50 categories, updated in real time, it defends against emerging threats like malware, phishing, coin mining, and Trojan attacks.
Designed for highly sensitive and regulated environments such as payment and healthcare industries, Azure Firewall Premium provides advanced threat protection through features like IDPS and TLS inspection to prevent the spread of malware and viruses across networks. To support the higher performance needs of these capabilities, it runs on a more powerful virtual machine SKU. Like the Standard SKU, it scales up to 100 Gbps, integrates with availability zones for a 99.99% SLA, and meets Payment Card Industry Data Security Standard (PCI DSS) compliance requirements.
Azure Firewall Premium includes the following features:
- TLS inspection: Decrypts outbound traffic, processes it, then re-encrypts and sends it to the destination.
TLS (Transport Layer Security) encrypts communications to ensure privacy, integrity, and authenticity, but this encryption can also conceal malicious activity. Without TLS inspection, Azure Firewall cannot analyze encrypted traffic, limiting threat detection. Azure Firewall Premium addresses this by terminating and inspecting TLS connections to identify, alert, and block threats in HTTPS traffic. It establishes separate TLS sessions with the client and the web server, using a customer-provided CA certificate to dynamically generate and present a replacement certificate to the client for secure inspection.
Azure Firewall without TLS inspection:
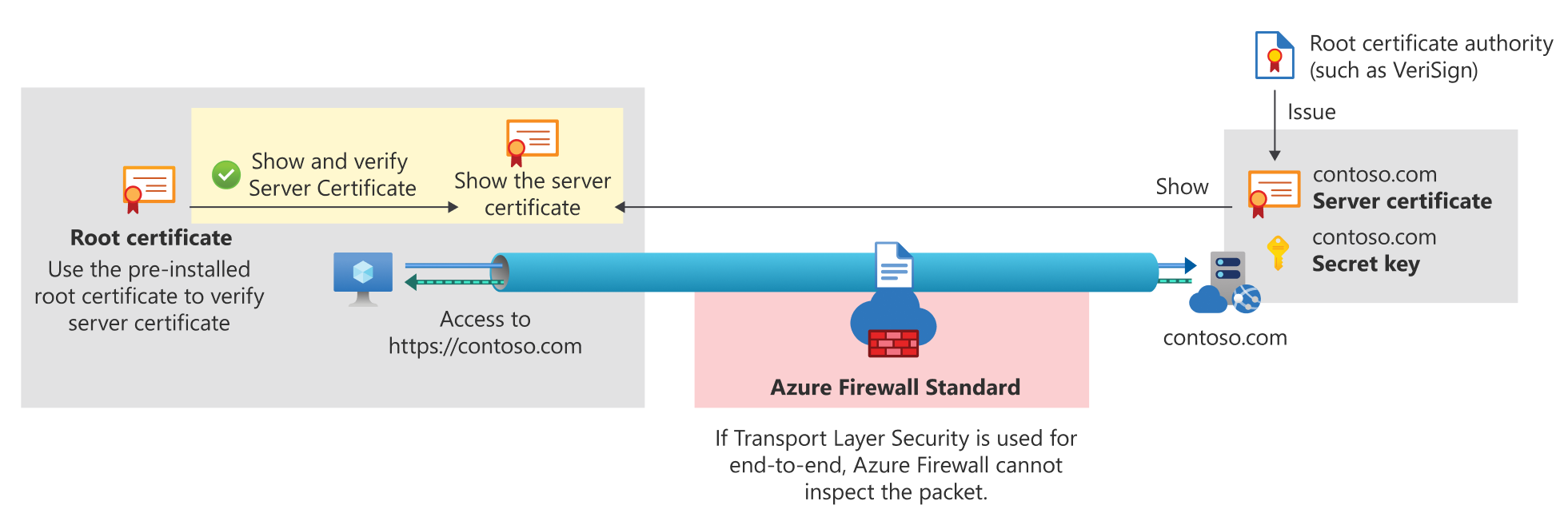
Azure Firewall with TLS inspection:
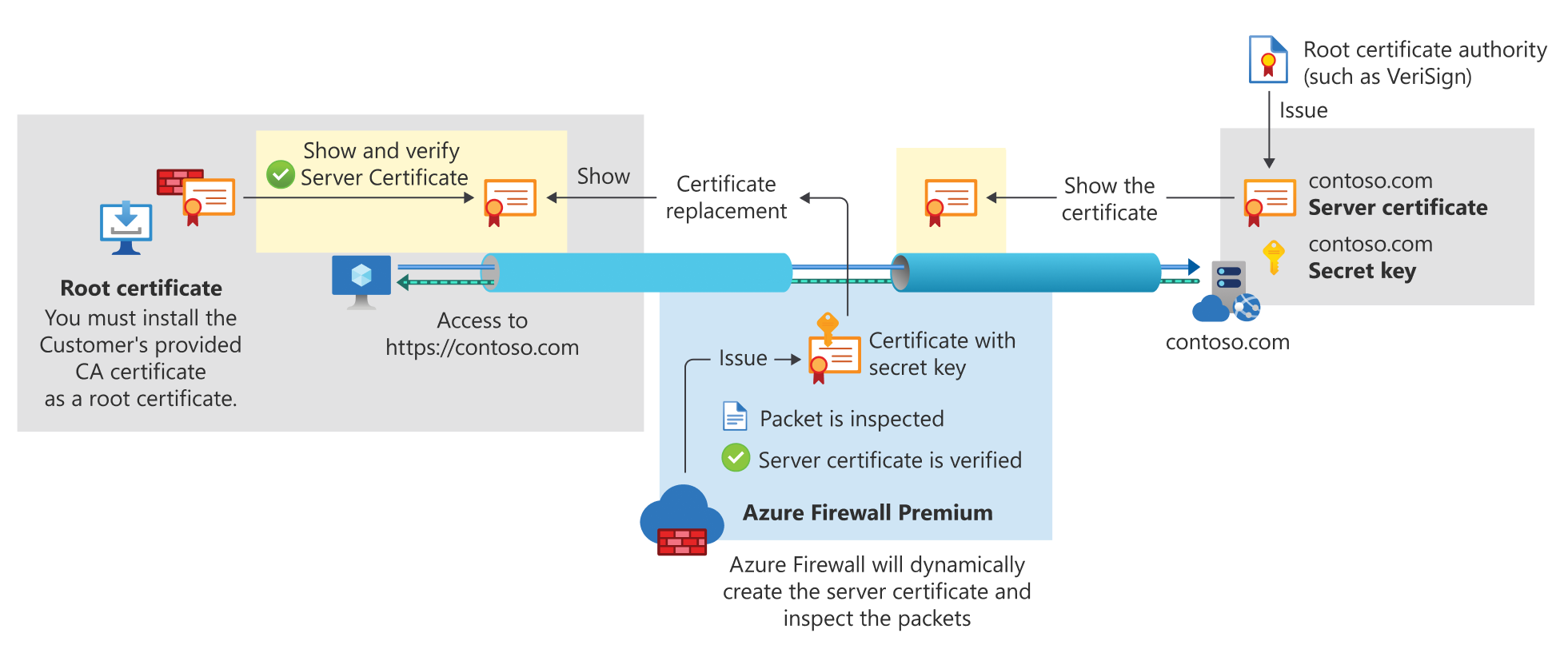
Azure Firewall supports outbound TLS inspection to block malicious traffic from Azure-based internal clients to the Internet, and East-West TLS inspection to protect Azure workloads from threats within Azure or between Azure and on-premises networks. For inbound protection, Azure Web Application Firewall on Application Gateway performs TLS inspection to safeguard internal Azure servers or applications from harmful requests originating from the Internet or other external networks, while ensuring end-to-end encryption.
- IDPS: Monitors network activities for malicious activity, logs information, reports it, and optionally blocks it. Azure Firewall Premium includes a fully managed, continuously updated, signature-based Intrusion Detection and Prevention System (IDPS) that monitors, logs, reports, and can block malicious activity. It detects attacks across Layers 3–7 by matching patterns such as byte sequences or known malicious code in both application and network traffic, covering inbound, outbound, and East-West flows, including on-premises connections. With over 67,000 rules in 50+ categories—such as malware command and control, phishing, trojans, botnets, vulnerabilities, and SCADA protocols—plus 20–40 new rules added daily, it delivers rapid, accurate detection with a low false-positive rate through advanced techniques like global sensor feedback loops. IDPS scans all ports and protocols for unencrypted traffic, while TLS inspection enables deep analysis of HTTPS traffic. Administrators can define private IP ranges for filtering and use an IDPS Bypass List to exclude specific IPs or subnets from inspection. Visit more information on https://learn.microsoft.com/en-us/azure/firewall/premium-features#idps
- URL filtering: Extends FQDN filtering to consider the entire URL, including any additional path.
- Web categories: Allows or denies user access to website categories such as gambling or social media.
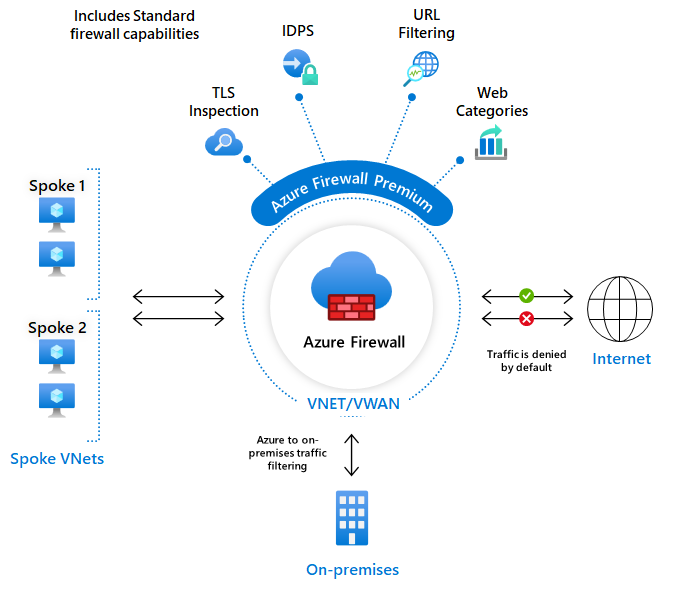
Tackling Real-World Challenges
One major challenge the customer faced was the prevention of lateral movement in the cloud network.
a common concern when dealing with breaches. Azure Firewall’s segmentation capabilities allowed us to implement strict network segmentation between different application tiers and environments, limiting exposure and attack surfaces.
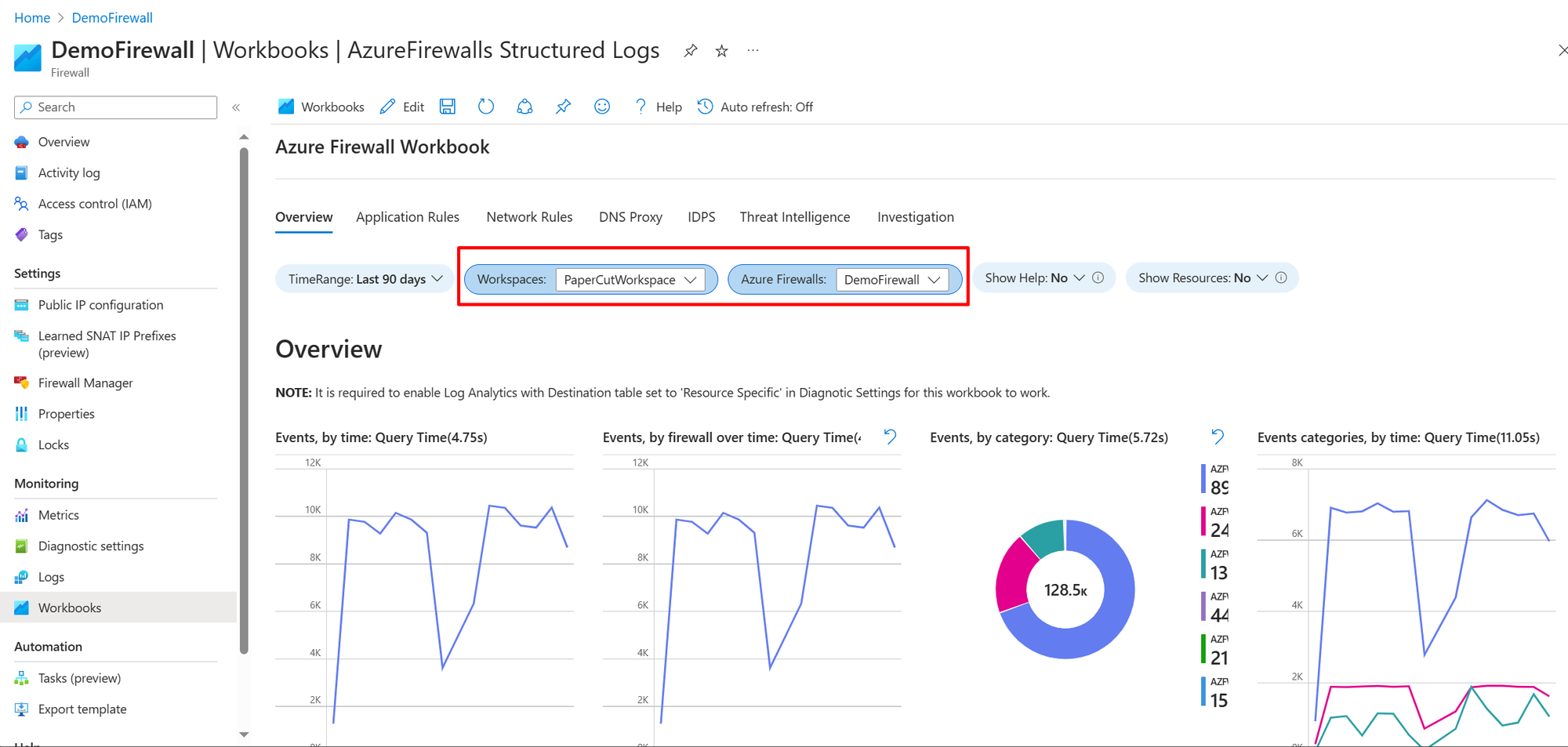
Monitoinrg and managing the infrastructure of the Azure Firewall
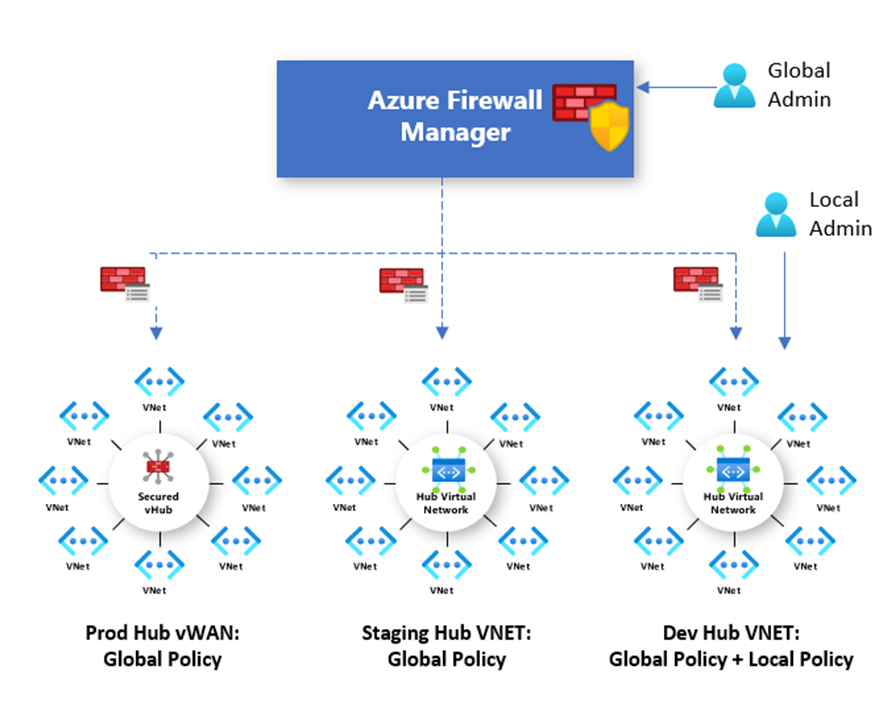
Another hurdle was managing policy consistency across multiple regions and subscriptions. Here, Azure Firewall’s integration with Azure Firewall Manager proved invaluable. It enabled centralized policy management and compliance adherence, simplifying governance for a sprawling multi-cloud footprint.
Plus, the customer benefited from the firewall’s native integration with Azure Sentinel for advanced security analytics, detection, and response, which helped in quickly identifying and mitigating potential threats.
Final Thoughts
My hands-on experience securing the customer’s Azure environment with Azure Firewall proved it is more than just a cloud boundary filter—it’s a sophisticated, scalable security platform. It addresses challenges traditional firewalls struggle with, such as scalability, integration, and threat intelligence.
For organizations migrating to or expanding within Azure, adopting Azure Firewall is a strategic move to fortify cloud defenses while simplifying management. The journey was a testament to how cloud-native security tools can empower businesses to innovate confidently in a secure environment.
If you are on a similar cloud security journey, I encourage you to explore Azure Firewall and see how it can transform your security posture with ease and efficiency.


