Securing Assets
When it comes to safeguarding digital assets, designing robust Network Security is like building a fortress amid a dynamic and ever-evolving battlefield. My approach weaves together with strategic segmentation, identity-centric controls, automation, and continuous monitoring, while each acting as a defensive wall, moat, or vigilant guard.
Network security refers to the practice of safeguarding resources from unauthorized access or attacks by applying controls to manage network traffic. Its primary objective is to ensure that only trusted and legitimate traffic is permitted. Azure provides a strong networking foundation to support application and service connectivity needs, enabling secure communication between resources within Azure, between on-premises environments and Azure, as well as between Azure and the internet.
The key areas that I ensure to align with the below areas:
- Foundations: Laying Down Azure Virtual Networks
- Traffic Controllers: Network Security Groups & Azure Firewall
- Defense-in-Depth: DDoS Protection & Monitoring
- Identity as the New Perimeter
- Encrypt Everything: Data at Rest & in Transit
- Automate for Resilience and Compliance
- Continuous Training & Recovery
- Governance & Accountability
By thoughtfully layering these strategies and tools, I build Azure networks that aren’t just secure but agile, maintainable, and ready to evolve. In the digital age, your fortress must be dynamic—combining the strength of technology, policy, and people in a single, resilient bulwark.
1. Foundations: Laying Down Azure Virtual Networks
At the heart of any secure Azure environment is the Virtual Network (VNet). This is your private, isolated network in the cloud. Each workload gets segmented into subnets, which not only helps with traffic management but also enforces security by limiting communication pathways.
Key practices that I follow:
- Subnet segmentation: Break workloads into distinct subnets to enforce boundaries.
- Private endpoints & Azure Private Link: Avoid public exposure by enabling internal-only access to resources (like databases or storage accounts) with Private Link, ensuring sensitive data never traverses the public internet.
- Service Endpoints: Restrict Azure PaaS services (like Azure Storage) to only your VNet, keeping communication internal.
2. Traffic Controllers: Network Security Groups & Azure Firewall
Network Security Groups (NSGs) act as the bouncers at every network door, controlling inbound and outbound traffic rules at both subnet and NIC levels. For broader traffic control and protection:
- NSG rules: Regularly review and apply the least privilege approach where it allows only the traffic that’s absolutely necessary.
- Application Security Groups: Organize VMs with similar functions and apply NSG rules at scale.
- Azure Firewall: Set additional perimeter rules, inspect traffic at Layer 7, and support outbound SNAT. Web
- Application Firewall (WAF): Protect web apps from common exploits and vulnerabilities on top of application gateways.
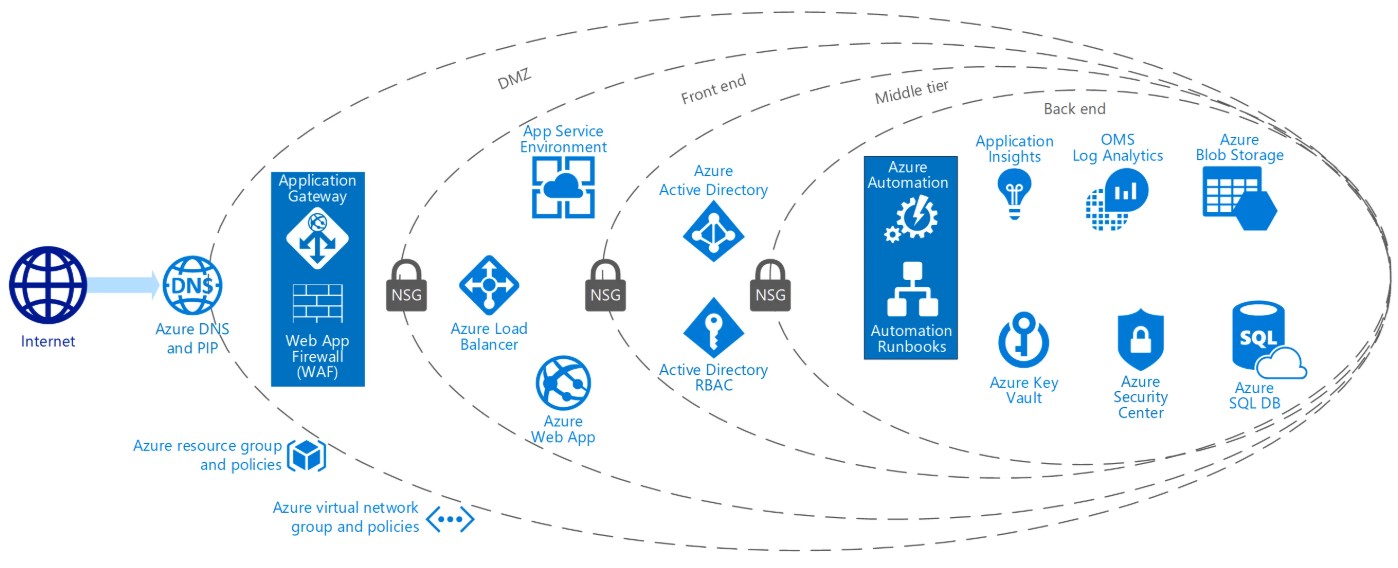
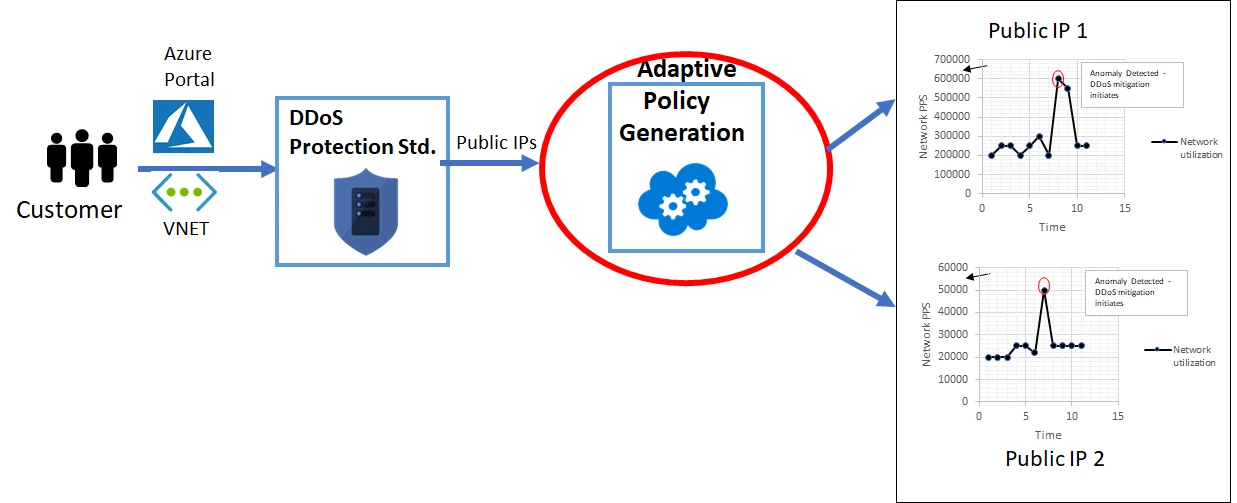
3. Defense-in-Depth: DDoS Protection & Monitoring
No fortress is safe from an army at its gates. Azure DDoS Protection is the automated flood barrier, detecting and muting large-scale attacks before they cripple services. For smaller threats:
- Intrusion detection & adaptive policies: Built into some Azure offerings, these help detect anomalies.
- Azure Monitor & Sentinel: Continuously watch network traffic, automate alerts on suspicious activity, and retain logs for forensic analysis.
4. Identity as the New Perimeter
I always initiate from the process of putting the Identity as the entry to the environment.
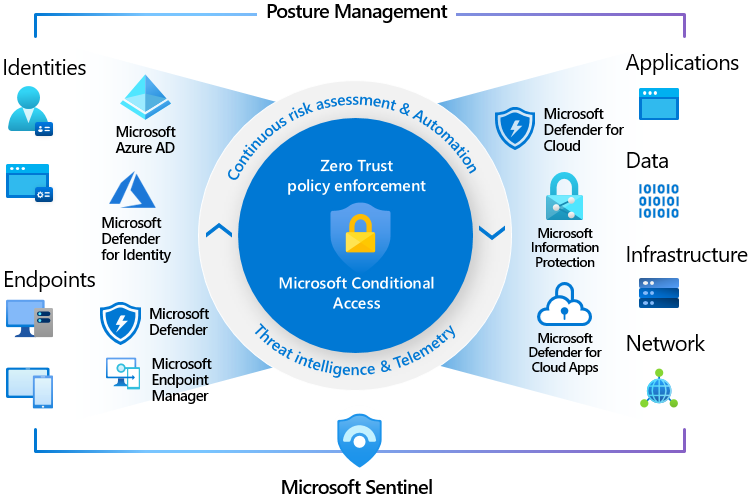
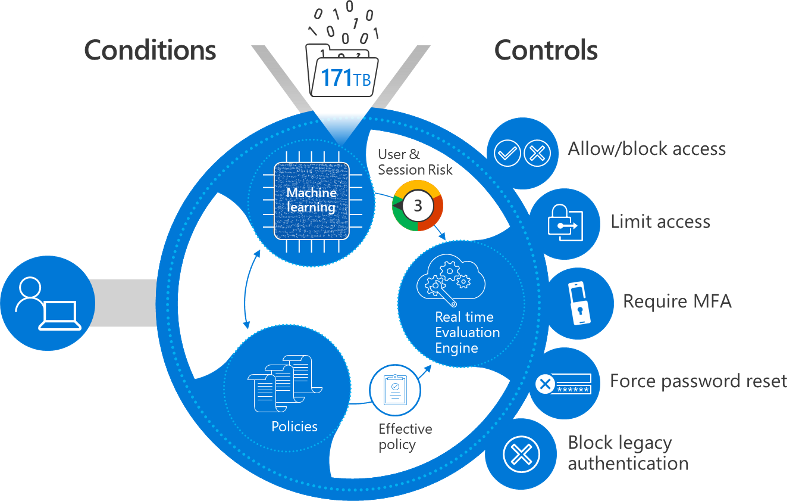
- Zero Trust Architecture: Assume breach, authenticate everything, authorize least privileges, and segment resources accordingly.
- Multi-factor Authentication (MFA): Enforce MFA for all users, especially privileged accounts.
- Conditional Access Policies: Grant or restrict access based on device, location, and risk context. \
- Role-Based Access Control (RBAC): Assign only the permissions required; regularly review and adjust
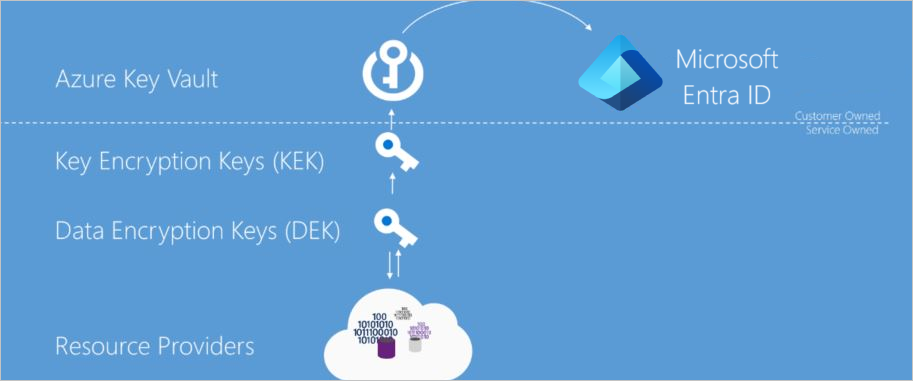
5. Encrypt Everything: Data at Rest & in Transit; Key Management
I always make sure the defenders that need a secure vault.
- Azure Key Vault: Centralized management and protection for encryption keys, certificates, and secrets. The storage location of the encryption keys and access control to those keys is central to an encryption at rest model. The keys need to be highly secured but manageable by specified users and available to specific services. For Azure services, Azure Key Vault is the recommended key storage solution and provides a common management experience across services. Keys are stored and managed in key vaults, and access to a key vault can be given to users or services. Azure Key Vault supports customer creation of keys or import of customer keys for use in customer-managed encryption key scenarios.
- Azure Storage Service Encryption & TLS: All data is automatically encrypted at rest; apply TLS to encrypt data in transit.
One of the biggest strengths of Microsoft Cloud is its flexibility. Whether an organization is looking for ready-to-use software, developer-friendly platforms, or full control over infrastructure, Microsoft provides solutions that fit every stage of the cloud journey.
- Software as a Service (SaaS): Think of tools like Microsoft 365—business-ready applications delivered securely from the cloud, with no need to worry about servers or updates.
- Platform as a Service (PaaS): For teams building their own applications, Microsoft offers powerful cloud-based services such as data storage, analytics, and messaging queues. These services help accelerate innovation without the complexity of managing underlying infrastructure.
- Infrastructure as a Service (IaaS): For organizations that want maximum control, IaaS makes it possible to run custom operating systems and applications in the cloud while still benefiting from Microsoft’s scalability, security, and global availability.
- Making Use of Microsoft Entra ID: Permissions to use the keys stored in Azure Key Vault, either to manage or to access them for Encryption at Rest encryption and decryption, can be given to Microsoft Entra accounts.
- Disk Encryption: Both Windows and Linux VMs benefit from Azure Disk Encryption built-in.
Refer to this link for more information: https://learn.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest
6. Automate for Resilience and Compliance
A stronghold weakens if human error creeps in. Automation is my silent sentinel ensuring the intrusion, detection and prevention:
- Azure Policy & Blueprints: Enforce compliance, auto-remediate misconfigurations, and ensure consistency across workloads.
- Just-In-Time (JIT) VM Access: Temporarily open access to management ports, shutting them automatically after a set period to reduce attack surfaces.
- Regular Patch Management: Use Azure Update Management to keep all workloads secure and compliant with the latest patches.
7. Continuous Training & Recovery
No defense is static, therefore, all my progressions will make sure that the the security enhancement should come with the new trends:
- Simulate Attacks: Regular “red team-blue team” drills help harden admin defenses and catch unseen weaknesses. (although this is a expensive process, however, it all depends on your workload).
One of the most effective ways to strengthen security is to test it against real-world threats. Red team–blue team simulations mimic how attackers operate (red team) and how defenders respond (blue team). These exercises go beyond theoretical audits as they expose vulnerabilities, test monitoring systems, and measure how well administrators respond under pressure.
While this approach can be resource-intensive and costly, the investment is often justified for organizations running critical workloads, handling sensitive data, or operating in highly regulated industries such as finance, healthcare, or government. Smaller organizations can still benefit by running scaled-down versions or by leveraging Microsoft’s built-in security assessments and penetration testing services as a starting point.
the term of Simulating Attacks can differ from Organizations; this is a process of cecking your security presence. - Automated Backup & Disaster Recovery: Leverage Azure Backup and test your restore process, ensuring services return swiftly after any breach
8. Governance & Accountability
This is where we map with the Companies goals, where the clarity in roles and processes ensures robust management.
Governance is a crucial part of management, which involves maintaining applications and their supporting resources across Cloud, on-premises, and other clouds. Azure provides a range of tools and services that work together to enable complete management. Resource management follows a lifecycle; from deployment, through ongoing operations, to eventual retirement.
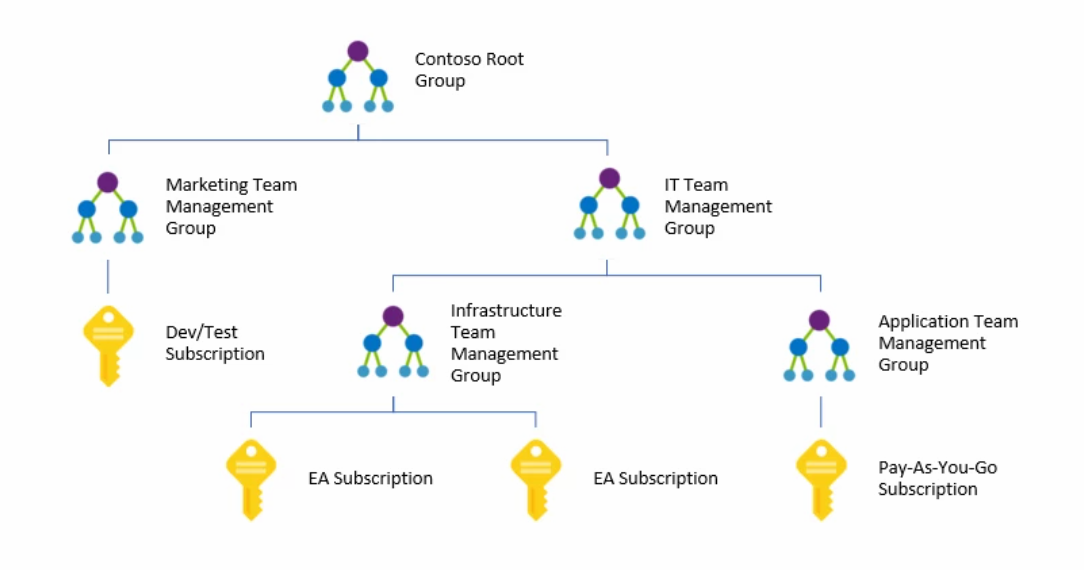
- Root Management Group: Apply broad policies consistently across the enterprise.
- Central Networking Team: Oversee core resources and avoid misconfiguration collisions.
- Regular Security Audits: External and internal audits keep your fortress up to standards and ready for new threats.
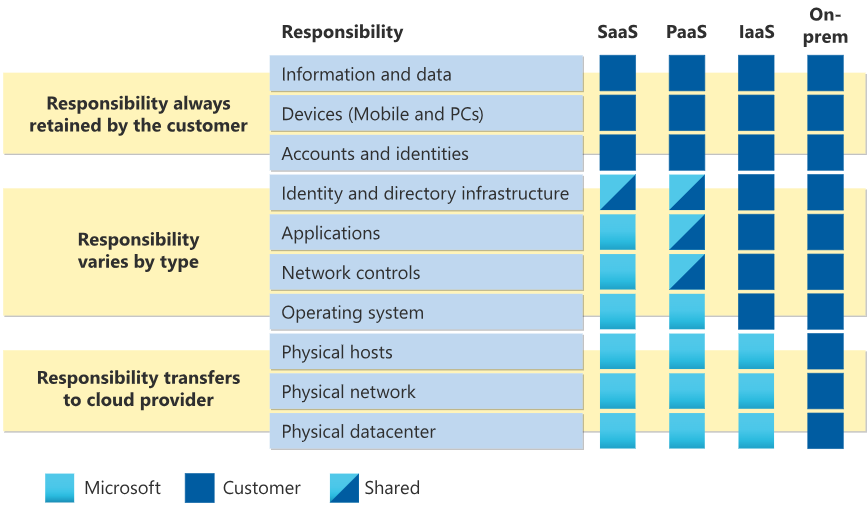
The Shared Responsibility Model: Know Your Boundaries
This is where we map with the Companies goals, where the clarity in roles and processes ensures robust management:
While designing a Cloud Environment, spcially an Azure environment, always ensure to secure the infrastructure although the Cloud Service Provider is gurantees it is solely our respon for securing your applications, data, and identities.
Moreover ensure to periodically review and update your responsibilities, train your teams on new threats, new features (like firewall auto-scaling), and compliance changes.
Experiences and Challenges I overcame
1. Protecting Web Apps with Application Gateway WAF
In one project, I deployed Azure Application Gateway with Web Application Firewall (WAF) in front of customer-facing web applications. The WAF was configured with OWASP Top 10 protection rules to automatically block SQL injection, cross-site scripting (XSS), and malicious bot traffic.
2. Hybrid Connectivity with Azure Firewall + VPN Gateway
For a multinational client, we built a secure hybrid cloud architecture by connecting their on-premises datacenter to Azure.
- Business Impact: This helped the client meet compliance standards while ensuring their e-commerce platform remained highly available during high-traffic promotions.
- Best Practice: Always run WAF in Prevention Mode (not just Detection) once you’ve tuned the rules, and integrate logs with Azure Monitor for real-time insights.
- The VPN Gateway established encrypted site-to-site tunnels.
- Azure Firewall was placed at the hub VNet to provide centralized traffic inspection and logging. This allowed them to extend their on-prem workloads into Azure with consistent security policies.
- Business Impact: The client gained a single pane of glass for monitoring inbound/outbound traffic, eliminated shadow IT risks, and ensured compliance with industry regulations.
- Best Practice: Use Hub-and-Spoke network topology with Firewall in the hub to simplify management and scalability.
3. Securing Remote Access with Azure Bastion
Previously, engineers accessed VMs via public RDP ports, which increased the risk of brute-force attacks. We replaced this approach with Azure Bastion, which provides browser-based RDP/SSH connectivity over SSL, without even exposing VMs to the public internet.
- Business Impact: The attack surface was dramatically reduced, no public IPs were needed for VMs, and IT admins could securely troubleshoot resources directly from the Azure Portal.
- Best Practice: Combine Bastion with Just-in-Time (JIT) VM access via Microsoft Defender for Cloud to enforce least-privilege, time-limited connections.
4. Mitigating DDoS Risks with Azure DDoS Protection Standard
For a financial services client running critical payment systems, we implemented Azure DDoS Protection Standard to automatically detect and mitigate large-scale Distributed Denial of Service attacks.
- It provided always-on monitoring, adaptive tuning, and real-time telemetry.
- During a simulated DDoS test, the service mitigated a 10 Gbps flood attack without any disruption to legitimate users.
- Business Impact: This gave the client confidence to move sensitive workloads to Azure while meeting banking sector compliance requirements.
- Best Practice: Pair DDoS Protection with a WAF and Traffic Manager for global resiliency.
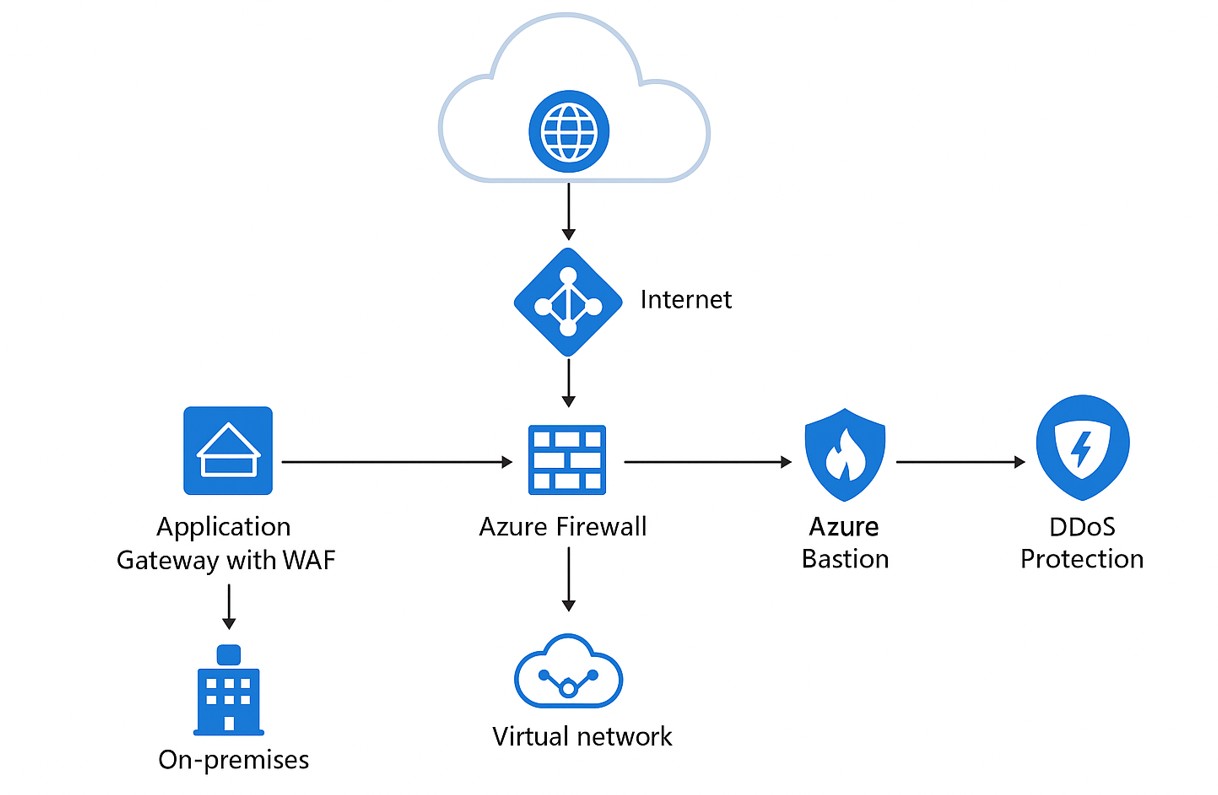
Used AI to generate the above Diagram
Conclusion
Securing workloads in the cloud is not about relying on a single tool, it’s about building a layered, adaptive defense. Azure Network Security brings together services like NSGs, Azure Firewall, WAF, Bastion, and DDoS Protection to create a robust security framework that grows with your business. By designing with Zero Trust principles, continuously monitoring threats, and adapting to new risks, organizations can transform Azure into not just a cloud platform, but a trusted foundation for long-term innovation and resilience.
Regardless of any Cloud Application, Solution, Service that you are to offer on any Cloud Service Provider, please ensure to follow the proactive mechanism rather than a reactive process.